For consumers and investors all across the world, the crypto realm has opened up dozens of new investing opportunities. However, with new opportunities come new risks.
The demand to store tokens safely in crypto wallets such as MetaMask, or Trust Wallet and hardware wallets such as Ledger or Trezor has only grown as the globe invests more in crypto. These wallets offer self-custody, which means users can keep their crypto in a secure environment where they alone have access to the assets.
In comparison to consumers handling their own wallets and private keys personally, any centralised, third-party holding user funds are typically regarded as less secure. Losing access to crypto assets as a result of a hack can be costly.

The owner of a hardware wallet and four separate Metamask “hot” wallets, u/PowerOfTheGods, detailed her experience with a classic wallet hack.
Before the new year, the user reported accessing Metamask to check the balances of all of their wallets. Everything appeared to be in order. The user recognised that every wallet had been wiped after checking again and finding one of their accounts displaying a zero.
“As I look at all of my wallets today, I see zero balances and I am absolutely crushed. It took all my power to even get out of bed, file reports, and write this post today.”
Here’s the Reddit post:
$ETH $MATIC $AAVE $TIME $ENS $OVR $AVAX $ZRX were among the cryptos that were stolen.
The user has been investing in digital assets since early 2016, and most likely has a good understanding of crypto and related operations, yet has nonetheless lost over $120,000 in cryptocurrency.
Because digital currencies are only run digitally, cryptocurrency holders and traders are particularly vulnerable to cyber-attacks. When it comes to wallet security, it’s best to take all of the basic safeguards when dealing with the crypto world since hacker tactics evolve.
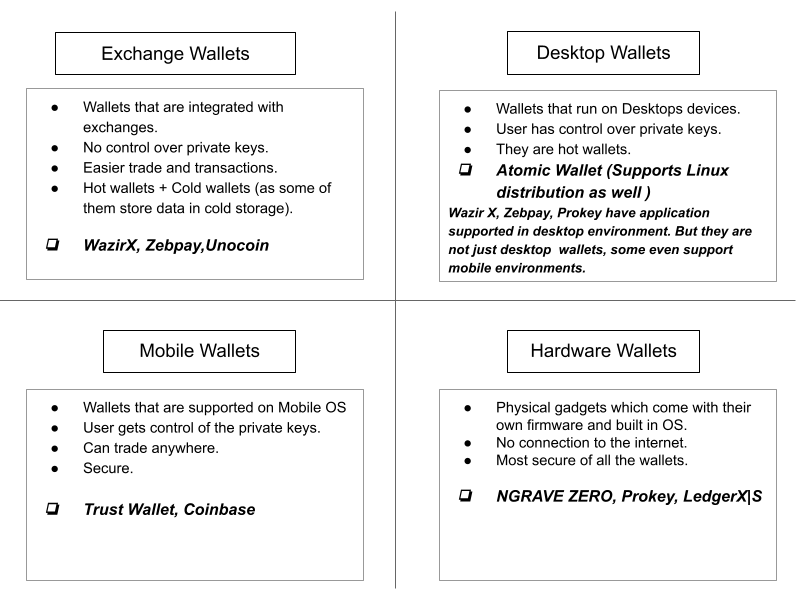
Crypto wallets can be software or hardware-based
Software wallets are known as hot wallets because they are generally connected to the Internet. Hardware wallets are sometimes known as cold wallets because they do not have an Internet connection.
Software-based hot wallets include MetaMask and Trust Wallet, whereas hardware-based cold wallets include Trezor and Ledger.
Hot wallets, which are always connected to the Internet, are regarded as less secure than cold wallets, which are always offline. Hot wallets, on the other hand, are still safer than keeping cryptocurrency on centralised exchanges.
ConsenSys Software’s MetaMask is a free-to-use cryptocurrency wallet. MetaMask is a blockchain-interactive software wallet that allows users to deal in cryptocurrency via a browser extension or mobile app.
MetaMask says that it has never been hacked, which appears to be true. However, this does not conform with all of the reports many have heard about people having their wallets emptied.
According to the victim, the only conclusion derived is while surfing the internet a malicious link might have been clicked. While using their Google Chrome browser (or Metamask addon), the virus must have managed to get control of their ledger.
Hackers target major operating systems like Windows and macOS with a variety of malware. Some viruses are designed to detect copied bitcoin addresses and replace them with hacker wallet addresses. In most cases, successful exchanges result in cryptocurrency being transmitted to unanticipated addresses controlled by hackers.
MetaMask may be completely unhacked, but that dubious website one might have visited last night may have installed malware on their PC. Now that a bad actor has logged your inputs, he or she has access to your password. Maybe they can take over your computer and reveal the secret word on your Metamask when you’re not logged in.
One of the dangers of storing your digital assets in a custodial account, sometimes known as a hot wallet – is the possibility of being hacked. If the site falls down, customers will be unable to transact cryptocurrency or log in to withdraw their funds, posing a significant danger.
Crypto hackers, unlike fiat scammers, do not discriminate based on the amount of your wallet. They’ll accept whatever they can get, whether it’s $5 or $50,000.
Tips to safeguard your crypto wallet:
- Try using different devices to transact your crypto as it would be best as it would prevent any malicious softwares to be downloaded on that device.
- Use a Non-Custodial Wallet-A non-custodial wallet is recommended if you have big crypto holdings and fear your funds are at risk of being compromised. Non-custodial wallets allow you complete control over your crypto wallet keys and are recommended if you don’t want third parties to have access to them.
- Using a non-custodial wallet, on the other hand, necessitates a larger level of responsibility in terms of key storage. If your crypto holdings are lost, you may lose them.
- Avoid Unregulated Exchanges – Keeping cryptocurrency holdings on an unregulated exchange is irresponsible. This is due to the fact that their security measures are frequently not up to par with regulated ones.
- Be extra cautious with your mobile traffic- Phishing efforts will only become more prevalent as cryptocurrency prices rise. Malicious apps, in addition to phishing, can acquire access to your mobile device and steal your login information. It may be difficult to believe, but malicious mobile apps may monitor what you input and even take screenshots of your screen.
- Use Two-Factor Authentication- If you maintain your crypto on a regulated exchange, you should utilise app-based two-factor authentication in addition to SMS verification to protect your account. This is because SMS-based 2FA is more readily hacked.
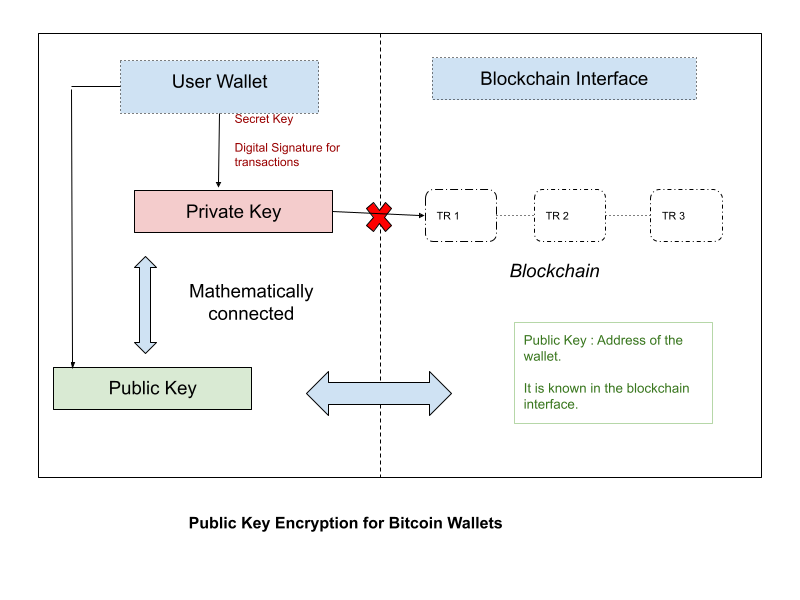
- Don’t share your private key: A user’s private key is their digital currency’s access code. Consider your public address as your email address and your private key as your user name. They can steal all of your cryptocurrencies if they have access to your private key.

When should you use hot wallets and when should you use cold wallets?
A cold wallet is similar to a typical savings account in that the coins are generally safe once they’ve been stored inside. Coins saved in a cold wallet, on the other hand, cannot be moved as rapidly as those held in a hot wallet – which may be fine for consumers who are just not avid traders or deal with crypto transactions on a regular basis. Hot wallets make it simple to transfer and receive cryptocurrency, but they also pose a higher risk than cold wallets, making them a double-edged sword for cryptocurrency users.
As more investors put their money into the small but rapidly developing market, crypto wallet security is becoming a top priority.











